Privacy & anonymity
Anonymity and privacy are two distinct characteristics. It's possible to achieve anonymity but not have privacy. Vice versa, it's possible to have privacy but not be anonymous.
In The Case For Privacy, David Friedman states privacy is "my control over other people's access to information about me".
Wikipedia defines privacy as "the ability of an individual or group to seclude themselves or information about themselves, and thereby express themselves selectively". Privacy, simply defined, means your activities are hidden.
Within computer science, anonymity and privacy are closely correlated. Wikipedia defines anonymity as "the state of an individual's identity, or personally identifiable information, being publicly unknown". Anonymity simply defined means "no identity". DarkFi creates on-chain anonymity using newly emerging cryptography.
In summary: privacy means our data is hidden. Anonymity means our identity is unknown.
Network vs. app layer
Blockchain privacy is primarily affected on two different layers of the architectural stack, the network layer and the application layer. The networking layer operates as a P2P network. This is how traffic moves around. By their very design, P2P networks are not private. Nodes need to connect to other nodes to pass traffic for the network to function.
Data must be transferred from one peer in the network to another. A party monitoring a transparent network can watch data propagate across the entire network. There are a few different solutions used for network anonymity. DarkFi currently has a Tor integration with future plans to support Nym.
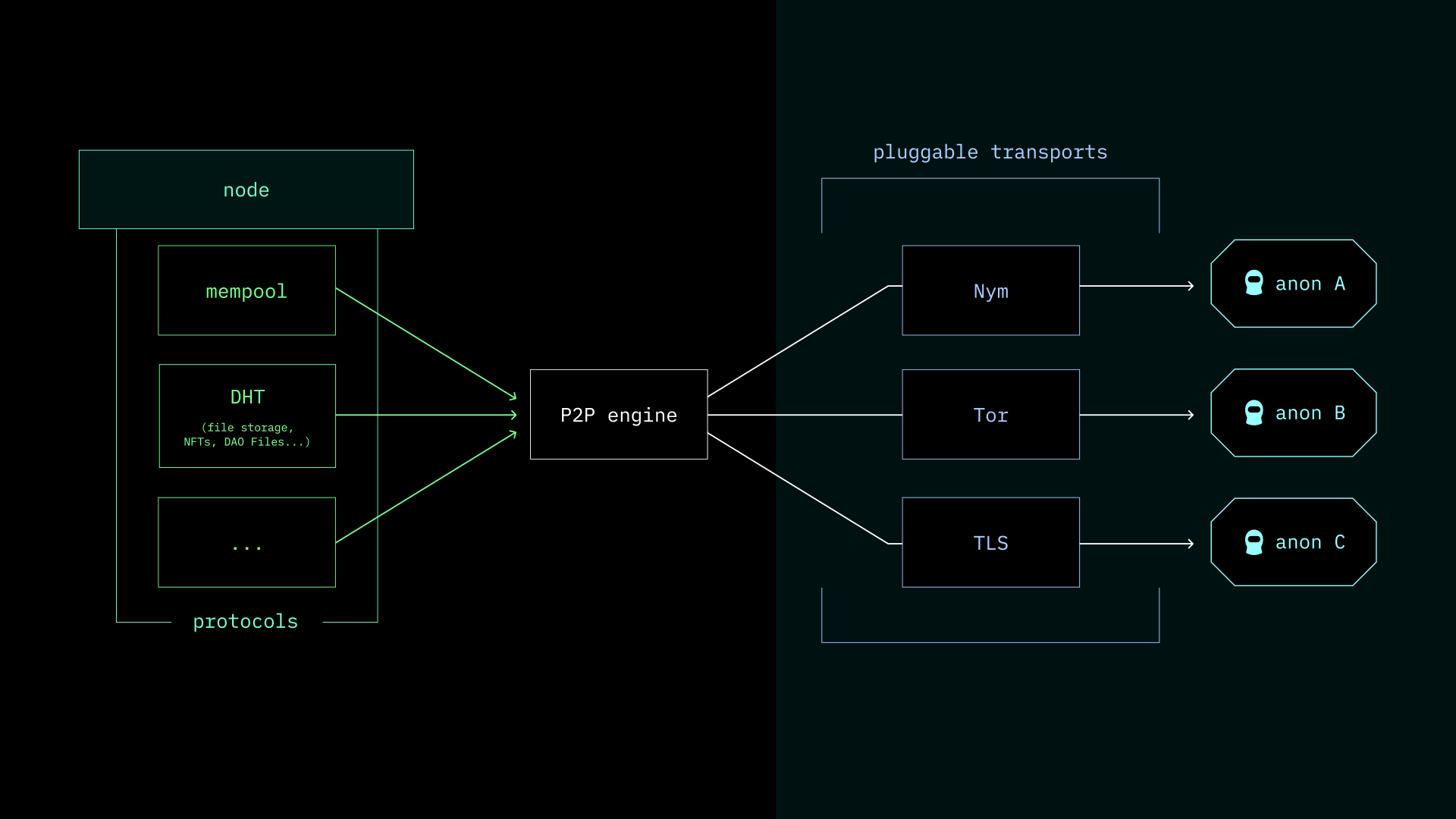
The application layer is how the user accesses the blockchain. A user interacts through applications, deploys smart contracts, uses wallets, and manipulates data. Most blockchains are transparent at this layer.
Full privacy1 on the application layer would need to consist of hidden interactions with an unlinkable identity. Full privacy on the network layer means no possibility of correlation to network traffic and identities.
Achieving anonymity
Zero-knowledge proving systems afford us the opportunity to achieve anonymity through privacy. By employing cryptographic techniques, like ZK proofs, DarkFi protects every part of a transaction. With every piece of the transaction hidden, outside observers have no way to identify participating parties.
ZK proofs work by calling a function and returning the result without revealing the input parameters. The entity verifying the info is only given a proof to validate. The verifier can see that the information provided is correct. Hence, the name "zero-knowledge".
Two interesting properties of ZK proofs:
-
ZK proofs are succinct. This means its quicker to verify the proof than it is to compute the input values.
-
ZK proofs can be ANONYMOUS.
There are scaling solutions, such as ZK rollups, that benefit from the first property.
The anonymity properties of ZK are what DarkFi is generally focused on.
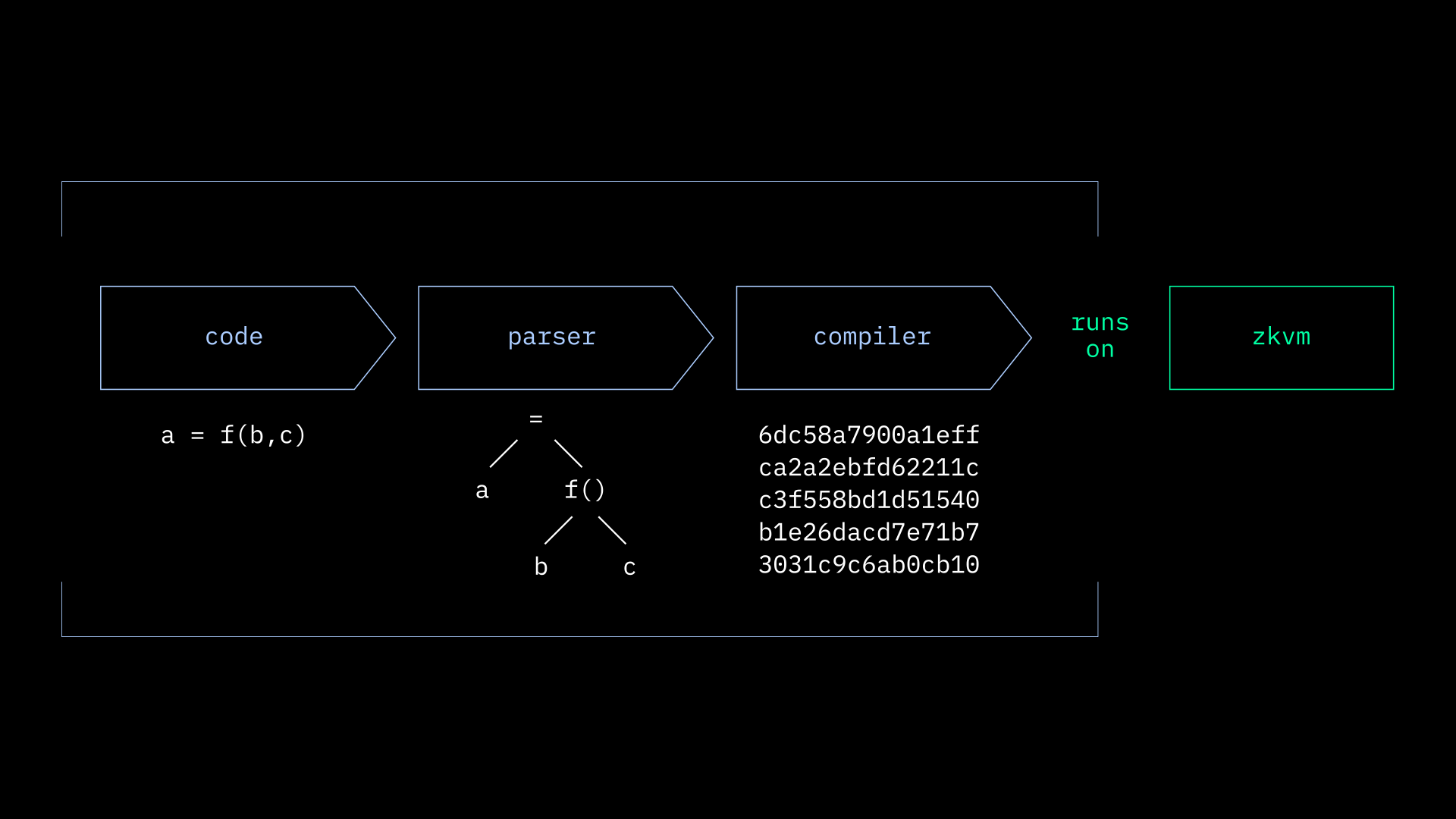
Proofs are written in a domain specific assembly language and compiled for the DarkFi zkVM that uses the Halo 2 proving system.
Enter anonymous engineering
Newly emerging cryptographic techniques are opening design spaces previously unattainable. Anonymous Engineering uses different schemes to create new anonymous primitives. Many of these primitives form integral parts within the DarkFi ecosystem.
A few cryptographic schemes used within anonymous engineering:
- polynomial commitment proofs - A prover can verify a polynomial has a certain property without revealing the polynomial, itself.
- multi-party computation - Multiple parties can perform calculations without each individual party revealing their inputs.2
- partial homomorphic encryption - You can perform computations on encrypted datasets while maintaining their confidentiality.
- anonymous inclusion proofs - Prove you're part of a data set without revealing your data & increase calculation speed.
The design choice for DarkFi's smart contracts are related to anonymous engineering.
Within DarkFi, the application logic and ZK proofs are deliberately separated to
make anonymity a conscious part of the dev process. The smart contracts on DarkFi
do not automatically have anonymity, but instead must be engineered with anonymity
in mind. Anonymous engineering3 is achieved when anonymous primitives are
combined with the app logic. The
native smart contracts
on DarkFi are examples of anonymous engineering. The proofs are written in a domain
specific language and then converted to bytecode by the zkas compiler for the
zkVM. The zkVM validates the proof.
Anonymous engineering applied
Crypto techniques, like the ones mentioned above, are used as building blocks to create anonymous application primitives. A few primitives that anonymous engineering unlocks:
- Anonymous Voting - uses anonymous inclusion proofs to prove the voter is in the merkle tree set and partial homomorphic encryption keeps the vote choice private. This is used within anonDAO.
- Anonymous Payments -
Anonymous payments on DarkFi are achieved using the sapling payment scheme.
Each transaction contains both a
MintandBurnphase. TheMintphase uses partial homomorphic encryption for the values and TOKEN ID. TheBurnphase uses partial homomorphic encryption for thevaluesandTOKEN IDand anonymous inclusion proofs to validate that the coin is present within the payment. TheMintproof creates a new coin, and theBurnproof is used to spend the previously minted coin.
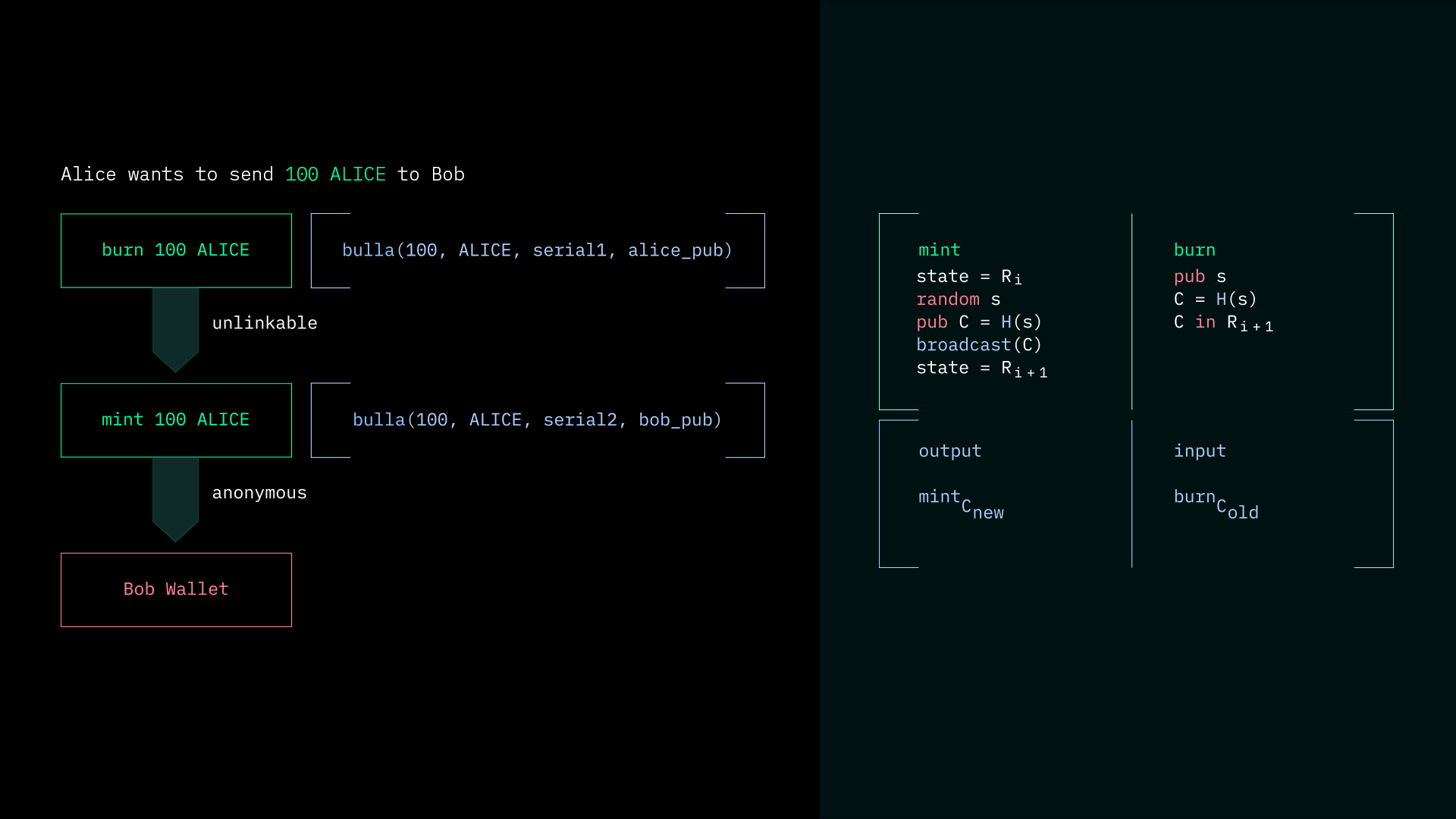
Payments are unlinkable with sender, receiver, and amounts hidden.
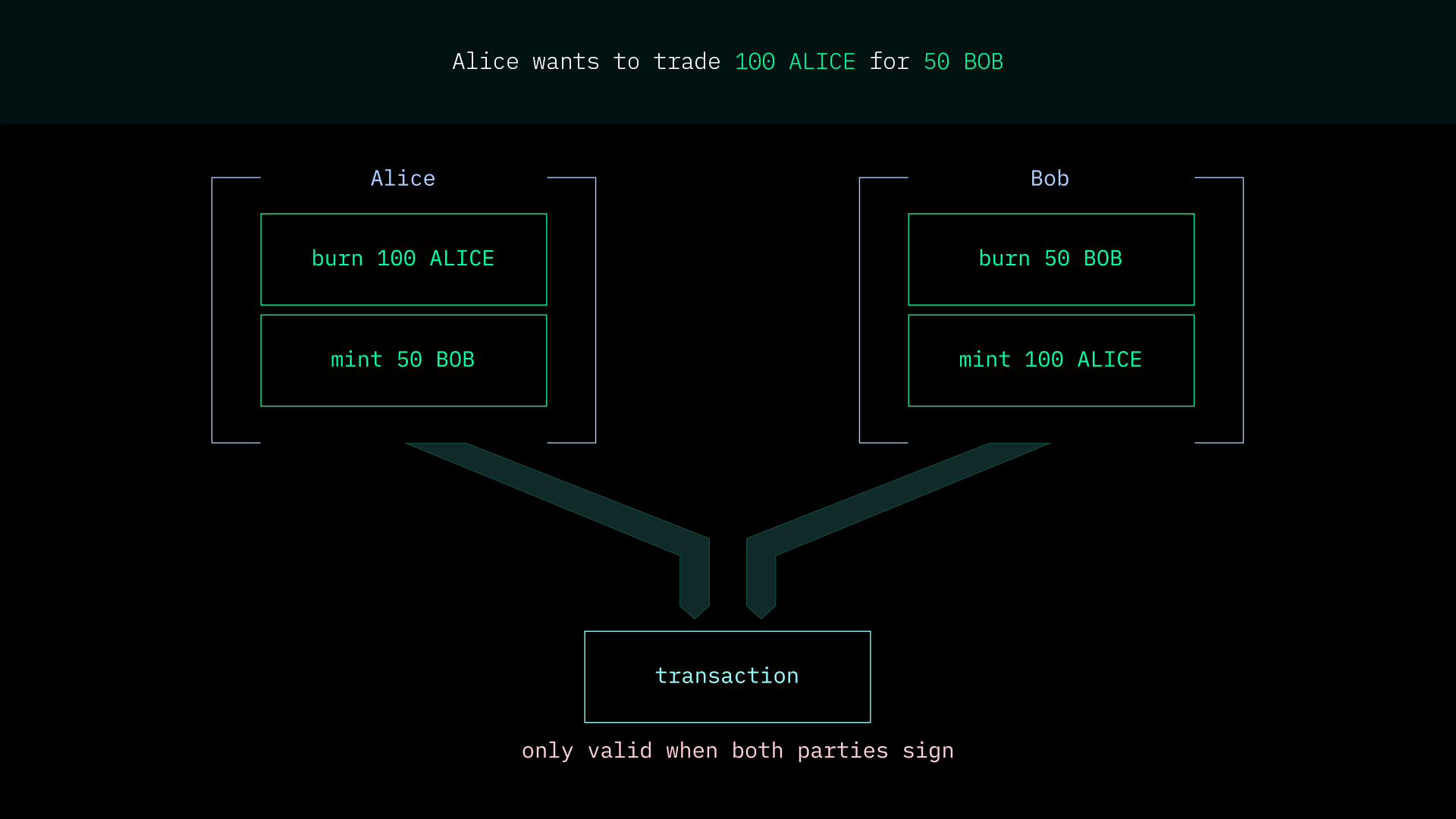
- Anonymous Atomic Swaps - More complex than the the anonymous payments feature, swaps brings two payment contract calls together to coordinate simultaneous payments. Swaps use partial homomorphic encryption and anonymous inclusion proofs. The transaction only becomes valid after both participants have signed the transaction.
- Anonymous Spam Protection (Rate Limit Nullifiers) - uses Shamir secret sharing scheme for the anti-spam feature.
Anonymity on the application layer is achieved through these engineering techniques.
The network layer achieves anonymity and unlinkability via traffic routing over anonymity networks. Full privacy on the DarkFi blockchain is achieved together with the application layer AND network layer (as mentioned in Achieving anonymity).
Anonymity in action
DarkFi's anonymous ecosystem is already active with applications for the public to get their hands on. DarkIRC, DarkFi's anonymous chat is live with unlinkable identities, encrypted direct messages, and decentralized over the DarkIRC P2P network. A pre-alpha mobile app is available and runs over Tor by default.
Join the movement
Tau is the encrypted task management system. It runs over the DarkFi P2P network, and supports anonymous routing networks. You can assign deadlines for tasks, rank order of importance, and create different workspaces, among other features. Collaborate with teams using Based CLI4.
Anonymous outgrowths
Anonymity creates many new opportunities5 that aren't possible on transparent blockchains. You can have unbiased, trustless and coercion-resistant on-chain interactions. The power to unlink identities empowers users. Off-chain physical risks due to on-chain identities disappear. Social attacks utilizing reputation like 'appeal to authority' becomes more difficult when there are no identities. Coordination will evolve.
DeFi markets experience significant friction due to their transparent nature. Front-running is an issue, exacerbated by total transparency into your market decisions. In many instances, users opt to use centralized exchanges that offer financial products similar to DeFi but better confidentiality when it comes to keeping user positions private. This is a failure of the ecosystem. Participants of the network can implement novel solutions using decentralized anon systems. More complex DeFi markets are enabled when using a fully private system.
DarkFi's codebase development also benefits from the anonymous ecosystem. You can contribute to the codebase anonymously. We can expand our reach and others can participate in using these anonymous primitives.
DarkFi is looking for experienced devs to help ship mainnet. Join DarkIRC and make your intentions known. Help us build the tech that crypto was always meant for.
Anonymous. Uncensorable. Sovereign.
As mentioned in The Status Quo in response to devs being targeted:
this is a hydra, because stronger technology is being developed and many more projects like Tornado Cash will come into existence. On many fronts this is already happening and communities are beginning to wake up.
This hydra is growing in strength. People can feel that something is amiss in their environment. This could be from self-reflection, witnessing their local communities falling apart, or watching the global order buckling under the weight of its own corruption. BUT there's a vibe shift happening. People are seeking out solutions.
However you arrive to this conclusion,
There is a path forward.
But it won't be handed to us.
Let's welcome the night together.
Let there be Dark.

-
Full privacy is achieving anonymity AND privacy. Both identity and actions are hidden. ↩
-
DarkFi is not yet using MPC. ↩
-
Anonymous engineering is the field in which anonymous primitives are implemented to build anonymity-enabling technology. ↩
-
A GUI for tau is currently in development. ↩
-
Timothy May was already discussing solutions anonymity would unlock when he wrote The Cyphernomicon in 1994. ↩